
SupplyChainis a Mess









Depi, the new and unique Security Tool that will show you exactly how attackers can break the links within your Software Supply Chain.
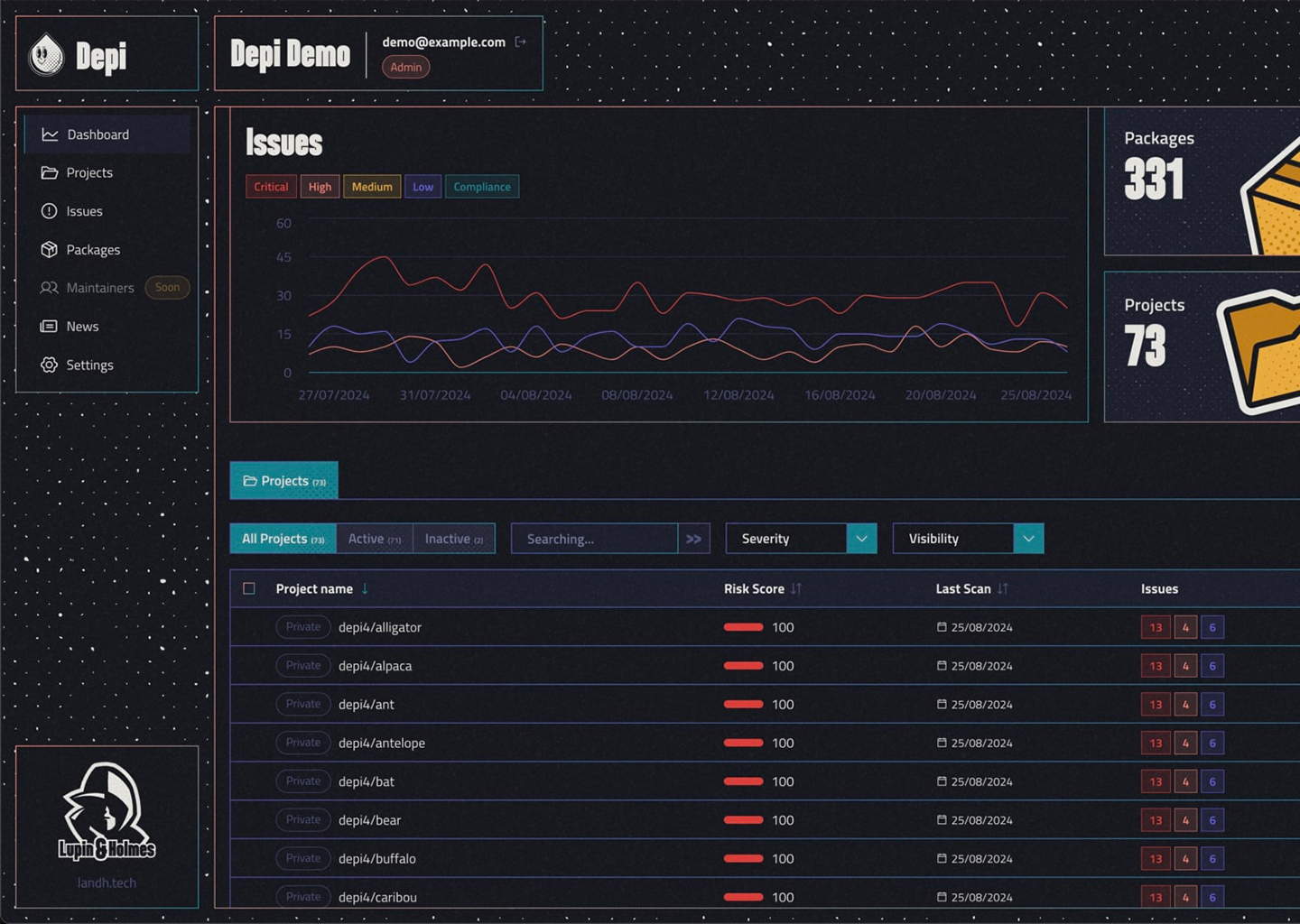



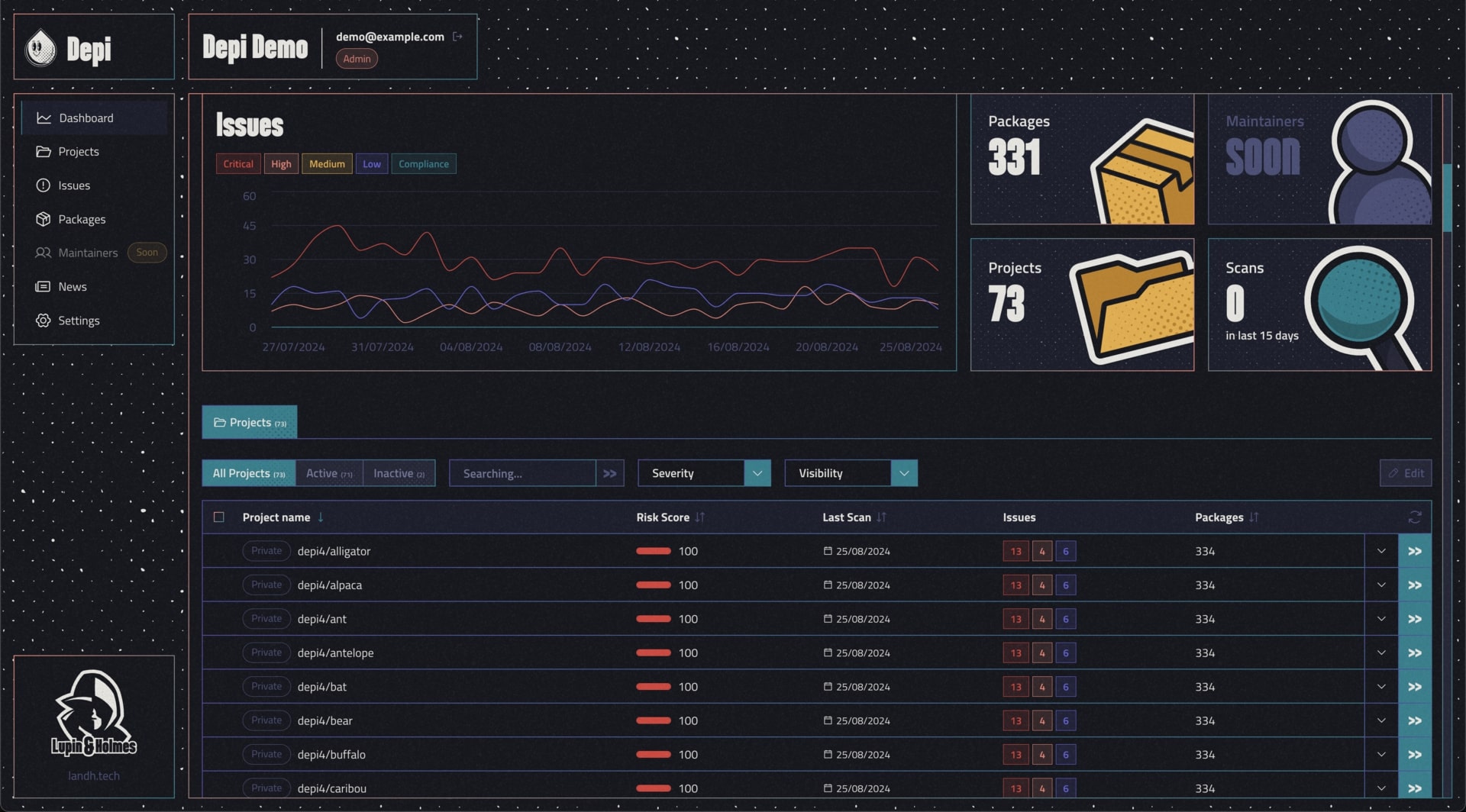
What Depi brings you?
Offensive security perspective
Think like an attacker, Depi uncovers the real-world tactics and techniques malicious actors use against your dependencies.
Easy to install
Get started in minutes and secure your software supply chain without adding complexity to your workflow.
Complete dependency tree scanning
Detect threats across your entire software ecosystem, from direct dependencies to deep transitive layers.
Risk-Based Prioritization
Focus on the issues that matter most. Depi scores threats based on severity, exploitability, and real-world attacker behavior, giving you a clear roadmap to remediation.
Focus on the issues that matter most. Depi scores threats based on severity, exploitability.
Supported technologies


Crafted from Real-World Experience
Depi was built by skilled hackers who uncovered real vulnerabilities and developed an effective tool that makes the difference in the Software Supply Chain.

- Access to Proactive Research
- Full Dependency Tree Scanning
- Upstream Maintainer Security
- Up to 100 Repositories
- Weekly Scan
- Access to Proactive Research
- Full Dependency Tree Scanning
- Upstream Maintainer Security
- 100 - 500 Repositories
- 72-hour Scan
- Access to Proactive Research
- Full Dependency Tree Scanning
- Upstream Maintainer Security
- Custom Repositories Number
- Custom Scan Frequency
Ready ?
Book a demo to see how Depi pinpoints the weak links in your software supply chain that attackers target. Discover how our tool helps you identify these vulnerabilities before they become a problem.
Book a demo
What's Up?


Depi is Now Available on AWS Marketplace !

Netflix Vulnerability: Dependency Confusion in Action




