Introduction
With modern software development relying heavily on open-source dependencies, protecting the software supply chain has become crucial. Each dependency carries risks, not only within its code but also from those maintaining it. A 2023 report from Anchore highlights the scale of this reliance, revealing that over half of all npm releases are maintained by just one person—out of more than 18 million releases with a single maintainer listed in their package.json file. This widespread dependence on a small number of individuals means that a company's codebase can be affected by any changes or compromises in the code they maintain.
This risk underscores the need for comprehensive protection. At Lupin & Holmes, we developed Depi, our Software Supply Chain Security tool, which evaluates both the links that we create with dependencies but also the maintainers behind each dependency. Depi helps to detect potential security threats, including account takeovers (ATOs), that could allow attackers to access and compromise downstream systems by gaining control over a maintainer’s account.
The Hidden ATO: Email Domain Takeover
One notable example of a maintainer ATO technique was described in 2022 by security researcher Matthew Bryant, who explained how attackers could take over npm maintainer accounts by exploiting expired email domains associated with those accounts. If a maintainer’s email domain expires, an attacker can purchase it, enabling them to trigger a password reset and gain access to the account. Once inside, attackers can upload malicious code into packages that downstream users may unknowingly incorporate.
When reading this in 2022, we immediately were intrigued by the simplicity and elegance of this technique. We thought that this behavior was fascinating. Even before the development of Depi, we wrote a piece of code back then that was checking for this kind of attack. We integrated this vulnerability check into Depi as one of the first. Depi monitors the status of maintainer email domains to detect possible account takeover risks.
In September 2023, we collaborated with our close friend and ethical hacker Snorlhax for the Bug Bounty Program of a high-profile target with over $25 billion in revenue and more than 20,000 employees. (Sidenote: The NDAs are getting frustrating. This explanation doesn’t show how cool the target is haha)
Using Depi, we gathered the email addresses of the company’s GitHub contributors and scanned them for any expired domains. The scan revealed a single contributor account with an expired email domain, yet the account remained active within the organization. We found that GitHub’s multi-email feature allowed a secondary, expired email to stay attached to the account, enabling the reset password link to work for the expired email domain even though it wasn’t the primary one.
VERY IMPORTANT: At this point we messaged the company and asked for EXPLICIT AUTHORIZATION to take over the account. Always ask explicit permission if you want to exploit such issues.
We bought the domain for a couple of dollars, and hit the reset password link. And lo and behold, we received the following:
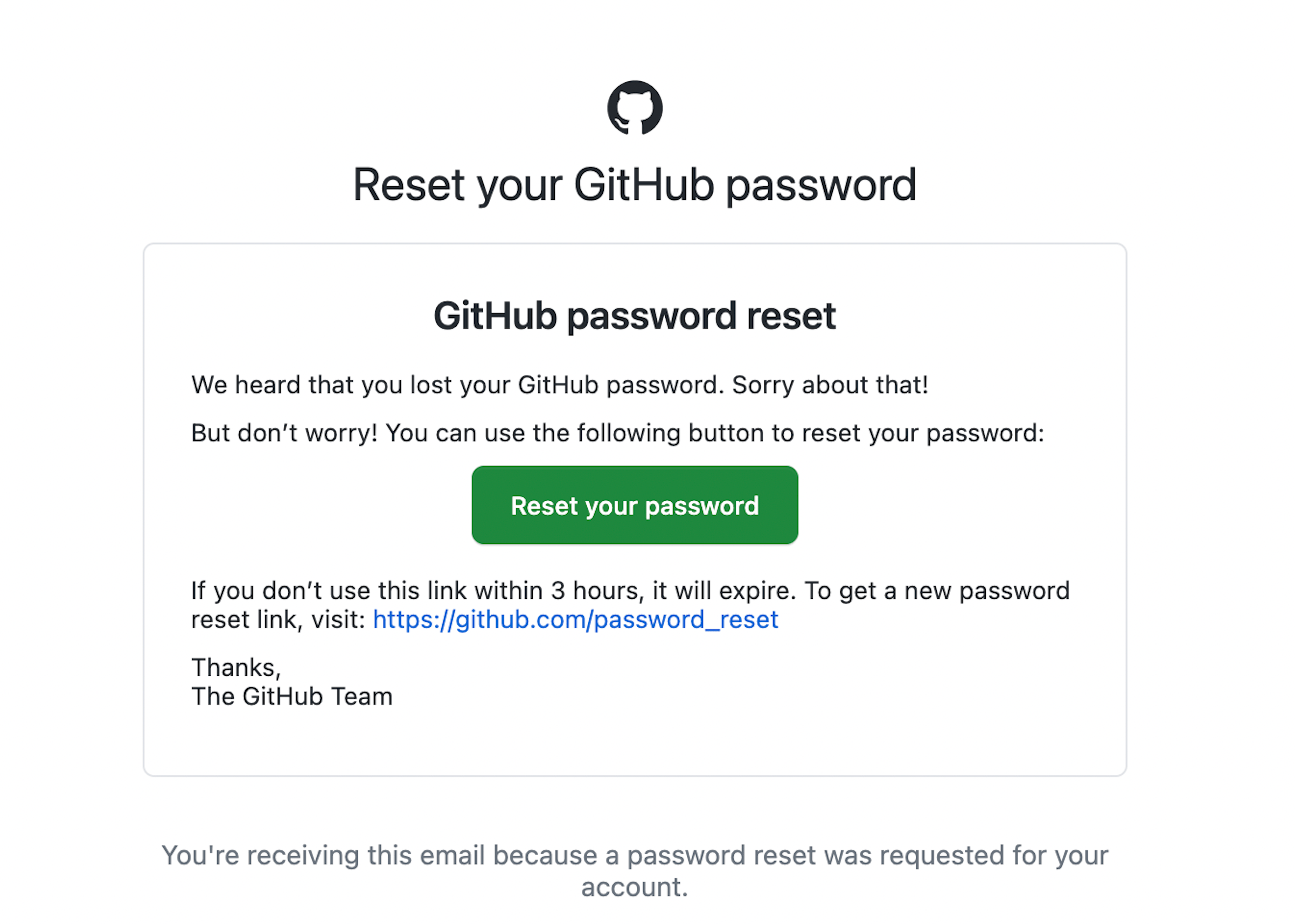
Once resetting the password, we connected to the Github account and … we were in.
This gave us access to internal source code, verifying the vulnerability. We reported our findings through the company’s Bug Bounty Program and received a $12,600 bounty for helping them address this security flaw.
Depi’s Latest Major Detection
Depi recently flagged a potential threat on the popular npm packages html-comment-regex, compare-func and array-ify alerting several of our customers who were using the packages. The alert stemmed from the discovery that the account of maintainer Steve Mao, a prolific contributor on npm with 171 package contributions and 167 owned packages, was at risk of an account takeover due to an expired email domain.
Indeed the email address [email protected] had the domain redacted.tld that expired, effectively allowing an attacker to potentially takeover Steve’s npm account. What happened is that the former company where Steve worked has been rebranded after he left and they dropped the domain.
We reached out directly to Steve Mao to discuss the potential vulnerability our scan had detected. Steve confirmed that while the expired domain was no longer connected to his primary npm email, a secondary email linked to that domain was still associated with his GitHub account. This setup could have enabled an attacker to exploit a password reset on GitHub, potentially leading to an account takeover. Steve took immediate action and removed the expired email from his account, effectively closing off this security gap. His quick response highlights the importance of proactive communication in maintaining supply chain security.
Steve’s packages collectively hold substantial reach, with ~709 million downloads all time and the following monthly downloads:
- compare-func: 25.2M
- array-ify: 22.9M
- html-comment-regex: 5.0M
- trim-off-newlines: 1.4M
- promise-to-callback: 348.4K
These packages had a cumulative download count of 54.8 million in just one month (in the last month when writing this article), illustrating the immense impact a single compromised account can have.
This situation serves as a reminder of the necessity for continuous monitoring and protective measures within the Software Supply Chain. Through real-time alerts, Depi enables our customers to stay protected and quickly respond to emerging threats, ensuring security even in high-risk, high-impact scenarios.
Steve Mao, the open-source maintainer affected by this issue, shared his perspective on the challenges developers face in navigating the evolving cybersecurity landscape:
"Security companies must continually adapt to keep pace with evolving tactics, as hackers today are relentless in discovering creative ways to exploit systems, often combining both social engineering and technical methods.
For developers like me, keeping up with these threats is a constant challenge. I hadn’t encountered attacks using expired email domains before, nor had I realized my own work email was expired—a valuable lesson in the importance of vigilance and regular updates.
This is where Lupin & Holmes excels, bridging the knowledge gap with their deep understanding of cybersecurity and a strong track record of success. Their team blends extensive experience with cutting-edge technology to proactively detect, prevent, and respond to complex security threats. Committed to safeguarding client data and systems, Lupin & Holmes has earned a reputation as a leader in cybersecurity, consistently staying ahead of emerging threats."
We want to extend our sincere thanks to Steve for his prompt response and collaboration in addressing this security risk. His swift action helped prevent a potential vulnerability from affecting countless users. We recognize the tremendous responsibility and dedication it takes to be a contributor in the open-source community, where maintaining and securing widely-used packages can often be a challenging, even overwhelming task. Steve's commitment to ensuring the security of his work is a testament to the vital role open-source maintainers play in safeguarding the software ecosystem, and we’re grateful for his partnership in keeping it secure.
Conclusion
The interconnected nature of the software supply chain means that any vulnerabilities within dependencies can ripple through an organization’s codebase. Our experiences with Depi’s security checks, from finding an expired email domain on a key account to monitoring popular packages at risk, highlight the value of scrutinizing not only the code but the maintainers behind it. By catching potential account takeovers before they become critical, Depi helps companies and Open Source maintainers reduce risk and strengthen the resilience of their software supply chains.