The state of Supply Chain Security
Modern software supply chains have grown far beyond a simple series of static steps. Today, the landscape is defined by interdependent systems where code flows from a developer’s local environment to remote repositories, through complex CI/CD pipelines, and finally to distributed registries. The SLSA framework offers one way to understand this complexity by breaking the process into three core components: source, build, and distribution.
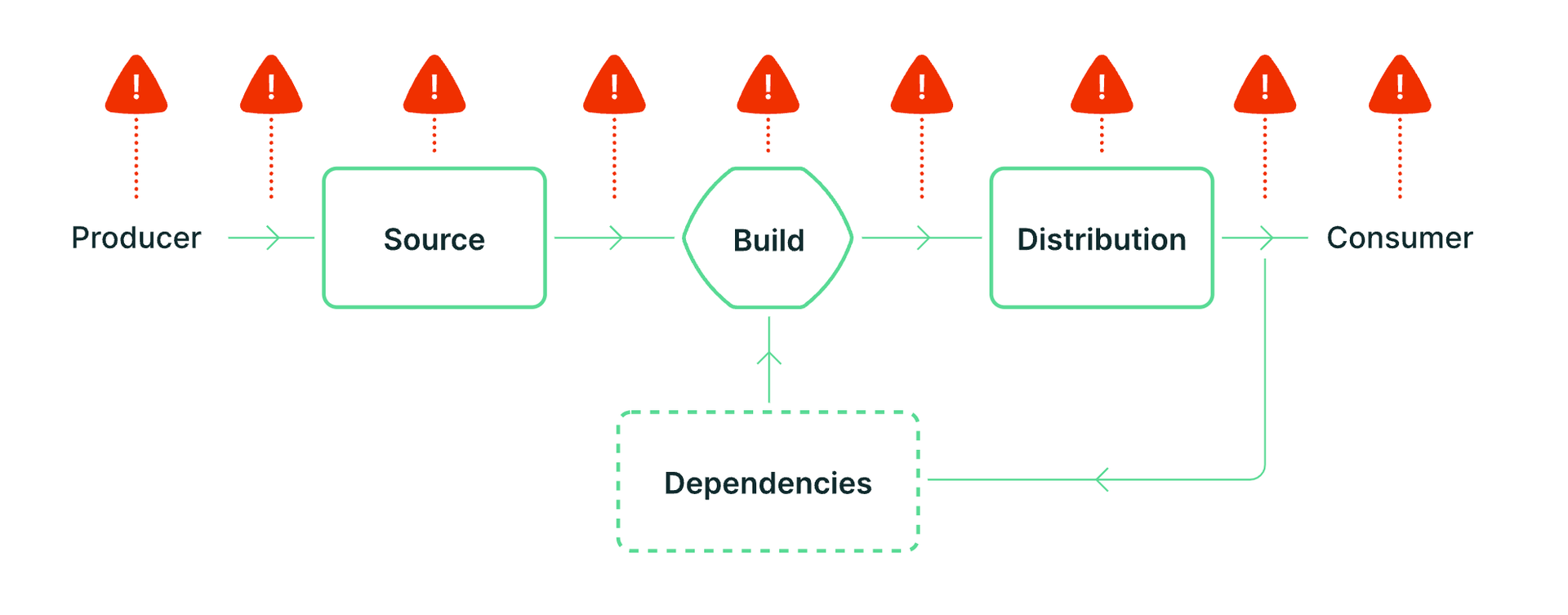
Each of these components introduces its own vulnerabilities. For example, popular platforms like GitHub and DockerHub are common entrypoints, while misconfigurations or exposed tokens within CI/CD pipelines can quickly lead to severe breaches. This intricate web of connections means that each dependency carries with it not only its own inherent risks but also the risk associated with the tools, processes, and maintainers that support it.
What adds another layer of challenge is the endless complexity created by dependencies themselves. Every dependency exists not only as a static entity on a registry but also as a dynamic component that traverses a CI/CD pipeline from a repository to its destination. In this journey, multiple links are forged, each with its own potential for vulnerability. The integrity of a dependency is further affected by the security posture of its maintainer, whose practices can either strengthen or undermine the entire chain. It is this network of intertwined connections that often becomes the weak point in an otherwise secure process.
Compounding the issue is the prevailing focus on defensive security. Many organizations rely heavily on software composition analysis solutions that function as firewalls, designed to catch malicious dependencies before they cause harm. While these tools provide a necessary line of defense, they often address only the symptoms rather than the root causes. By concentrating on blocking known threats, the industry tends to overlook the fundamental problem, understanding how these dependencies and their complex links can be compromised in the first place. A deeper, more proactive approach is needed, one that scrutinizes every connection within the supply chain to identify and remedy potential vulnerabilities before they are exploited.
Offensive Security Perspective
Our approach is firmly rooted in an offensive security mindset, a philosophy that drives us to seek out vulnerabilities rather than simply building walls against known threats. We are not a defensive security company; our mission is to conduct innovative research in the software supply chain security field, specifically to detect entrypoints for backdoors before they can be exploited. Rather than relying on passive defenses, we actively pursue vulnerabilities by leveraging extensive bug bounty hunting as a sandbox for our research. For those who may be unfamiliar, bug bounty programs offer rewards to independent security researchers for identifying real-world vulnerabilities. Every discovery made through these programs feeds directly back into our development process, creating a virtuous cycle where research informs development, and our enhanced tools, in turn, enable deeper research.
This proactive, iterative loop not only strengthens our technology but has also proven to be an effective funding strategy. In fact, Les Echos, the first daily French financial newspaper, published an article on how we raised 500 thousand dollars through our research-driven approach, which helped us develop the MVP of Depi.
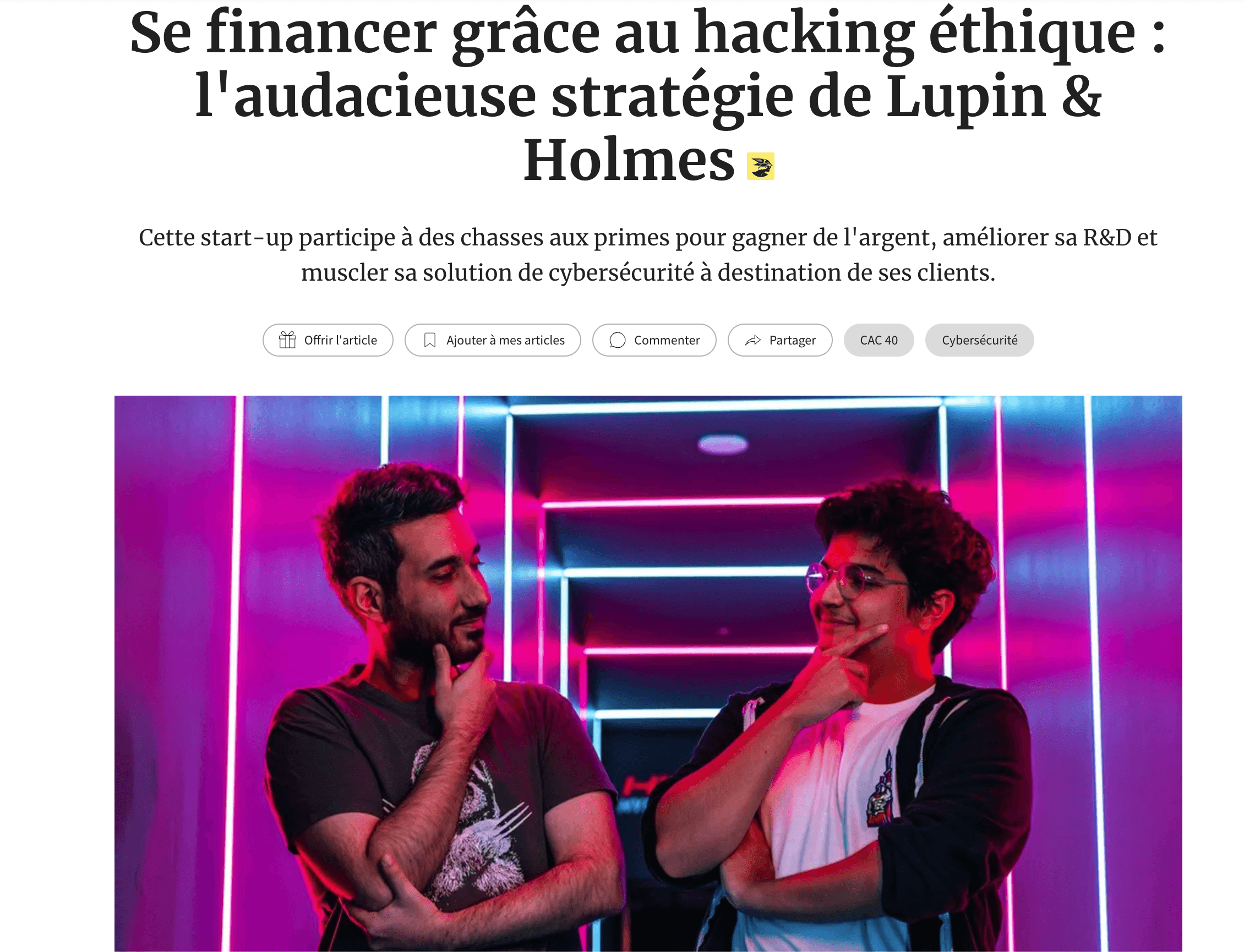
Our offensive security research is demonstrated by a series of high-profile initiatives. One notable example involved an email takeover of a maintainer with 700 million installations, achieved by claiming an expired domain linked to his email. This vulnerability had far-reaching impacts, affecting major FAANG companies and the broader Web3 industry.
Steve Mao, the open-source maintainer affected by this issue, shared his perspective on the challenges developers face in navigating the evolving cybersecurity landscape:
"Security companies must continually adapt to keep pace with evolving tactics, as hackers today are relentless in discovering creative ways to exploit systems, often combining both social engineering and technical methods.
For developers like me, keeping up with these threats is a constant challenge. I hadn’t encountered attacks using expired email domains before, nor had I realized my own work email was expired—a valuable lesson in the importance of vigilance and regular updates.
This is where Lupin & Holmes excels, bridging the knowledge gap with their deep understanding of cybersecurity and a strong track record of success. Their team blends extensive experience with cutting-edge technology to proactively detect, prevent, and respond to complex security threats. Committed to safeguarding client data and systems, Lupin & Holmes has earned a reputation as a leader in cybersecurity, consistently staying ahead of emerging threats."
In another instance, we hacked a Fortune 500 company by backdooring HashiCorp, which led to a bounty of $17,000. We also uncovered a critical vulnerability by compromising developers’ laptops, CI/CD builds, and production environments via an exposed DockerHub organization, resulting in a bounty of $50,500. Moreover, our discovery of a Cache Poisoning vulnerability on registry.npmjs.org, one that had the potential to crash npmjs.org and destabilize the entire JavaScript ecosystem, earned us a bounty of $10,500. These examples, among many other research findings that will be disclosed soon, highlight why we position ourselves as an offensive security R&D company rather than mere maintainers of a SaaS platform. By relentlessly probing the software supply chain, we not only expose vulnerabilities but also innovate continuously to fortify the ecosystem against future threats.
Depi’s not
Before explaining what Depi offers, it is crucial to clarify what it is not. We are not a defensive security company that simply builds walls to block known threats. Unlike traditional Software Bill of Materials (SBOM) tools, Depi does not just catalogue components or act as a passive record of assets. We are not an attack surface management (ASM) solution or a static application security testing (SAST) tool that focuses solely on the source code. And we don't perform a conventional source code analysis of your dependencies. Instead, we focus on deconstructing the links that allow vulnerabilities to propagate within the software supply chain. Our intent is not to add another layer of defense but to address the root issues that allow these vulnerabilities to exist in the first place.
What does Depi do ?
Depi takes a proactive stance in software security by dissecting and breaking the links within the software supply chain. At its core, Depi examines the entire dependency tree rather than relying solely on lockfiles. This comprehensive approach allows us to capture both static and dynamic relationships between components. We analyze not only how dependencies are defined in manifest files but also the specific artefact definitions, the chosen registries or artifactory sources from which they are pulled, and the intricate relationships between a dependency, its originating repository, and the maintainer's own security practices.
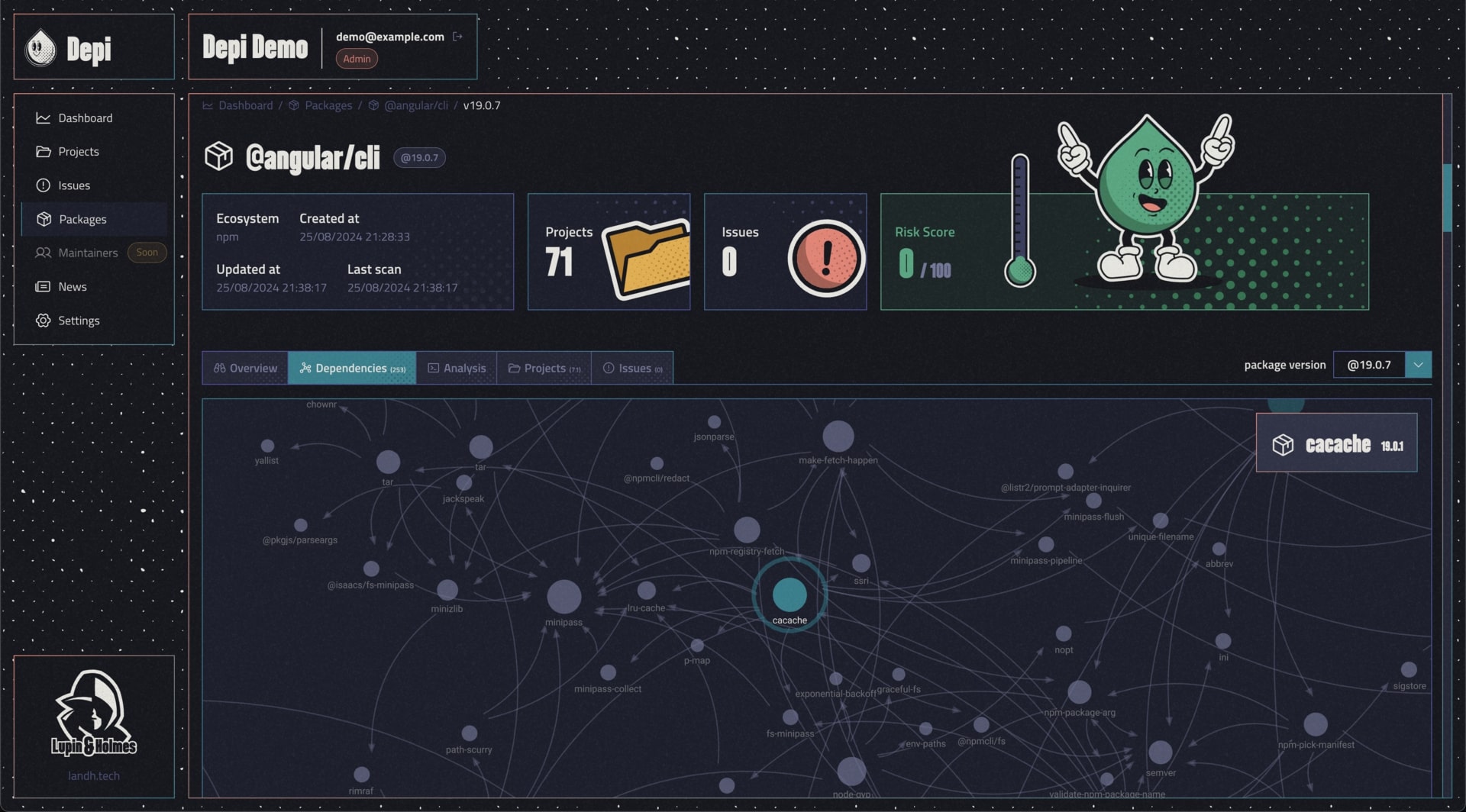
Every dependency creates multiple links within your system. These links refer to the ways dependencies are specified in your project files, the points of origin from which they are fetched, and the continuous connections maintained between the dependency, its source repository, and the maintainer’s security measures. By mapping these relationships, Depi uncovers the weak links that could be exploited by malicious actors before any breach occurs.
As a SaaS platform, Depi seamlessly integrates with popular version control systems such as GitHub and GitLab, enabling us to automatically check all manifest files and artefact definitions across your repositories. This integration ensures that the entire software supply chain is continuously monitored and evaluated, providing developers and security teams with actionable insights that allow them to fix vulnerabilities at their source rather than merely defending against their consequences.
What does Depi scan for ?
Depi’s scanning process is engineered to have the maximum observability when securing your software supply chain. Many existing solutions rely solely on static lockfiles to determine which dependencies will be installed; while this is a useful starting point, it only offers a partial view of your system. Lockfiles capture a single moment in time, missing the dynamic interactions and updates that occur throughout the development lifecycle. Furthermore, some package managers, such as pip, do not generate lockfiles by default, highlighting the limitations of conventional approaches.
To address these gaps, Depi resolves both the lockfiles and the entire dependency tree. This dual approach means that we not only identify the intended packages from a lockfile perspective but also uncover every component and sub-dependency that plays a role during runtime. We examine every manifest file and artefact definition to ensure that no dependency is left unexamined.
Beyond cataloguing packages, our scanning extends to the security posture of each maintainer and the CI/CD systems associated with every dependency. We map out every link created along the chain, the way dependencies are specified, the points of origin from which they are fetched, and the ongoing relationship between a dependency, its repository, and the maintainer’s security measures. Any misconfiguration, confusion or subtle alteration that could compromise the integrity of a package is flagged. This comprehensive, holistic approach ensures that potential vulnerabilities are identified early, giving security teams the actionable insights they need to address issues before they become exploitable risks.
Thanks to all the Design Partners so far
The development of Depi has been a truly collaborative journey, built on the innovative spirit of our early bug bounty hunting efforts. We initially used bug bounty programs as a sandbox for testing and exploration, which not only exposed critical vulnerabilities in the software supply chain but also brought together a vibrant community of security researchers. This early phase of experimentation allowed us to refine our techniques and ultimately led to the creation of a dynamic community of design partners, all driven by the same passion for uncovering and fixing hidden risks.
Our community spans a remarkable spectrum of industry leaders. From FAANG companies to Fortune 500 enterprises and visionary start-ups, every decider, security engineer, and DevOps professional we reached out to provided invaluable insights. Their expertise and real-world experience have been instrumental in shaping the features and functionalities of Depi, ensuring that our solution addresses the practical challenges faced by organizations across the board.
Our research journey began in 2021, inspired by groundbreaking work such as Alex Birsan’s research on Dependency Confusion. His work laid the foundation for our approach, igniting our curiosity and driving us to explore the depths of software supply chain vulnerabilities. The insights we gained during this early phase became the blueprint for the robust, proactive security measures that Depi now offers.
The development phase kicked off in late 2022, marking the transition from research to a fully realized product. Over the course of several months, we integrated the feedback from our community, refined our scanning techniques, and built a platform that could comprehensively address the challenges of modern software supply chains. Today, Depi is ready to launch, being the culmination of persistent innovation and collaborative effort.
We extend our deepest gratitude to everyone who has been part of this journey. Every contribution, every conversation, and even the many quirky questions we received helped us to see the problem from new angles and to develop creative, effective solutions. Your support and candid feedback have been essential in driving our progress and ensuring that Depi meets the real-world needs of today’s security landscape.
Now, with Depi launching, we are ready to take our offensive security mindset to the next level. We are not just here to patch vulnerabilities or react to threats, we are here to fundamentally reshape how software supply chain security is approached. Together, we are ready to hack the planet in the best possible way: by breaking everything ;D
Learn More
If you want to dive deeper into how Depi can transform your approach to software supply chain security.
Book a demo today. Our team is ready to walk you through our proactive scanning approach, show you how we break the links within your dependency chain, and share the innovative research that drives our platform